The internet, a vast digital world that has become an essential part of our daily lives, is filled with endless opportunities—from career advancements to cat videos. But beneath the surface lies a darker side: security threats, data breaches, and the misuse of personal information. These dangers strike fear into anyone who values their online safety, making a comprehensive security system more critical than ever.
If you’re running an Ubuntu server, security isn’t just a luxury—it’s a necessity. That’s where CSF (ConfigServer Security & Firewall) comes in. This powerful, user-friendly firewall is here to make your life easier and keep your server safe from harm. If you’ve been searching for a reliable way to fortify your server’s defenses and streamline your security management, you’re in the right place.
Why CSF
When it comes to choosing a security solution for your Ubuntu server, there are plenty of options out there, but CSF (ConfigServer Security & Firewall) stands out for several reasons. First and foremost, CSF is known for its simplicity and effectiveness. It offers a user-friendly interface that makes configuring and managing your firewall a breeze, even for those who aren’t seasoned security experts. With CSF, you can quickly set up rules to control incoming and outgoing traffic, helping to protect your server from unauthorized access, DDoS attacks, and a variety of other online threats.
Beyond its ease of use, CSF is highly customizable and rich in features. It includes built-in intrusion detection, IP blocking, and login failure detection to keep your server secure. Plus, it integrates seamlessly with popular control panels, making it an excellent choice for web hosting environments. CSF is not just a firewall; it’s a comprehensive security suite that adapts to your needs and adds layers of protection without overcomplicating your setup.
Install CSF on Ubuntu
For this guide, we’re using Ubuntu 24.04 as our server of choice. But don’t worry, if you’re running Ubuntu 20.04 or 22.04, this guide applies to those versions as well. Why? Because we’re using apt, the default package management tool for Ubuntu. It’s easy, reliable, and perfect for installing and managing software packages on any Ubuntu system. You’ll be surprised at how smoothly the process goes—ready to jump in? Let’s get started!
Update Packages
Before we dive into the fun part of installing CSF, let’s start with a little housekeeping. Your Ubuntu server needs to be well-fed and up-to-date. Trust me, an outdated server is like going to battle with a rusty sword. To update your system, open your terminal and enter the following commands:
sudo apt update sudo apt upgrade
Run these commands regularly to keep your system in tip-top shape. Not only does this help with installing new software smoothly, but it also patches any lurking vulnerabilities. So, think of it as a quick yoga session for your server. Namaste.
Install CSF Firewall
With your Ubuntu system polished and primed, it’s time to roll out the red carpet for CSF. Installing CSF isn’t rocket science, but I’ll make sure it feels like a walk in the park.
Download the Latest Version of CSF
First up, we need to grab the latest version of CSF straight from its source. Run the command below to download CSF:
wget https://download.configserver.com/csf.tgz
Why wget, you ask? Because it’s the digital equivalent of saying, “Hey, internet! Give me that file!” And it delivers. If you don’t have wget installed, you can get it with:
sudo apt install wget
Extract the CSF Archive
Like unwrapping a gift, the next step is to extract the downloaded tarball (yes, that’s what cool people call it):
tar -xzf csf.tgz
“Tarball” sounds way more exciting than just “archive,” doesn’t it? It almost makes server administration sound like an adventure.
Navigate to the Extracted Directory
To set things up, we need to go into the CSF directory we just extracted. Type:
$ cd csf
This is your command-line equivalent of stepping into the CSF workshop.
Run the Installation Script
The moment of truth! Run the installation script to set up CSF on your Ubuntu server:
sudo sh install.sh
Cue the drumroll… and voilà! CSF is officially on your system. But hold on, don’t pop the champagne just yet. We need to make sure it’s properly installed.
Verify the Installation
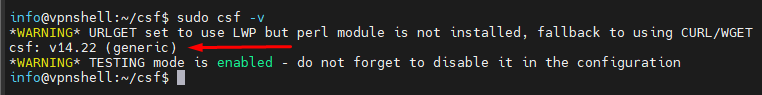
Check if CSF is ready for action by running:
sudo csf -v
If everything went smoothly, you should see the version number of CSF pop up like a proud badge of honor.
By now, you’ve updated your system, downloaded CSF, extracted it, and installed it. Give yourself a pat on the back—you’re doing great!
Configuring CSF Firewall
Now that CSF is installed, let’s move on to the juicy part, CSF firewall configuration. A firewall without configuration is like a bouncer at a club without a guest list—confused and useless. CSF offers extensive configuration options to help tailor the firewall to your specific security requirements. Here are some crucial settings:
ICMP_IN
Setting ICMP_IN to 1 allows incoming ICMP requests, such as ping. This is helpful for public-facing services to verify availability. Setting it to 0 blocks these requests entirely.
ICMP_IN_LIMIT
The ICMP_IN_LIMIT parameter controls the rate of incoming ICMP requests per IP address within a set time frame. The default value (1/s) suffices for most use cases but can be adjusted if needed.
DENY_IP_LIMIT
DENY_IP_LIMIT sets the maximum number of IPs that CSF can block. Keeping this number manageable ensures server performance isn’t compromised.
DENY_TEMP_IP_LIMIT
Similar to DENY_IP_LIMIT, DENY_TEMP_IP_LIMIT applies to temporary blocks. It’s recommended to set this lower than DENY_IP_LIMIT.
PACKET_FILTER
PACKET_FILTER helps filter invalid or malicious packets before they hit your server. Enabling this strengthens security and reduces potential attack vectors.
SYNFLOOD Protection (SYNFLOOD, SYN_FLOOD_RATE, SYN_FLOOD_BURST)
These settings protect against SYN flood attacks that can overwhelm your server. Only enable if you suspect or know of such attacks, as they may slow connection setup.
CONNLIMIT
CONNLIMIT restricts the number of active connections per port. Example:
22;5;443;20
This allows up to 5 connections on port 22 (SSH) and 20 on port 443 (HTTPS).
PORTFLOOD
PORTFLOOD limits connection attempts within a set timeframe. Example:
22;tcp;5;250
This configuration blocks an IP if it makes more than 5 connections to port 22 (TCP) within 250 seconds. The block is lifted after 250 seconds of inactivity.
Configuring Open Ports
Restricting the number of open ports enhances server security. By default, CSF has various open ports, such as:
It’s advisable to remove unused ports to minimize risk. Below are recommended configurations for common services:
- Basic Server:
- Apache:
- FTP Server:
- Mail Server:
- MySQL (Remote Access):
Managing IP Addresses
Blocking and allowing IP addresses are fundamental firewall functions.
Blocking IPs
To block an IP, edit the csf.deny file:
Add each IP or range on a new line:
Allowing IPs
To allow an IP to bypass blocks, add it to the csf.allow file:
Example entries:
Ignoring IPs
To exclude an IP from filtering, add it to the csf.ignore file:
Example:
Applying Changes
After any modifications, restart CSF to apply updates:
Testing CSF Configuration
CSF operates in testing mode by default. Change this by setting TESTING to 0:
Verify configuration changes:
Conclusion
With CSF standing guard, you can rest easy knowing your server is shielded by a robust firewall, ready to fend off digital troublemakers. And even if the unexpected happens in the wee hours of the morning, at least you can be confident your server’s defenses are on high alert.
Remember, maintaining server security isn’t a set it and forget it task. Regularly revisiting and fine-tuning your CSF configuration ensures your system stays fortified against evolving threats. So, keep tweaking, stay vigilant, and may CSF keep your server safe and sound—day and night!
FAQs
Q: What is CSF, and why do I need it?
A: CSF (ConfigServer Security & Firewall) is a powerful and customizable firewall for Linux systems. It offers features like login failure detection and various security enhancements. You need it for better protection against cyber threats and to manage your server’s traffic like a pro.
Q: Is CSF free to use?
A: Yes, CSF is free and open-source. It’s a fantastic tool for improving server security without breaking the bank.
Q: Can CSF be used alongside other firewalls?
A: While CSF can technically coexist with other firewalls, it’s recommended to use it as your primary firewall to avoid conflicts.
Q: How do I know if CSF is active?
A: Run sudo csf -l to list the current rules and check if CSF is actively monitoring your server.
Q: How do I disable CSF temporarily?
A: Use the command sudo csf -x to disable and sudo csf -e to enable it again.

